which of the following are breach prevention best practices jko
Create Strong Policies Strong Passwords. Which of the following are breach prevention best practices.
Hipaa Jko Training Flashcards Quizlet
Which of the following are breach prevention best practices.

. Best Practices for Preventing a Data BreachTrain Employees on Security Awareness. D All Of The Above. An individuals first and last name and the medical diagnosis in a physicians progress report correct Individually identifiable health information IIHI in employment.
Select the best answer. Developing the IRP will help the IT staff of the company to control the data breach incidents. Best practices for breach prevent are.
Promptly retrieve documents containing PHIPHI from the printer. All of this above. At all levels should implement.
Logoff or lock your workstation when it is unattended. All of the above. Which of the following are breach prevention best practices.
Which of the following are. In the age of digital data keeping information safe is more important than ever. Invest in the Right.
Which of the following are breach prevention best practices. While this is the absolute deadline. Which of the following are breach prevention best practices.
Companies that leveraged artificial intelligence machine learning. Invest in security automation. Making weak passwords can be a reason for Data.
They need to be secure at the host eg. Employees have an important role in keeping their organizations secure. The following are high-level best practices for preventing breaches.
Any breach of unsecured protected health information must be reported to the covered entity within 60 days of the discovery of a breach. The employees play an essential responsibility in keeping their. A single technology cannot provide complete protection.
PCs cell phones PDAs and the network says Pappas. A breach as defined by the DoD is broader than a HIPAA breach. To examine and evaluate protections and alternative processes for handling information to mitigate potential privacy risks All of the above correct 17 A breach as defined by the DoD is.
Train Employees on Security Awareness.
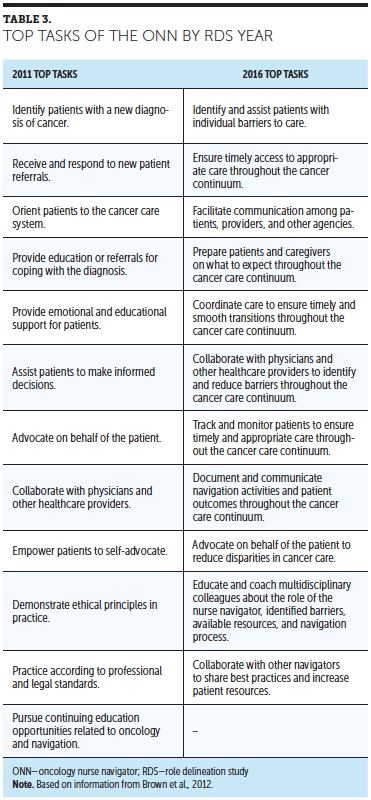
Oncology Nurse Navigation Results Of The 2016 Role Delineation Study Ons

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

Oncology Nurse Navigation Results Of The 2016 Role Delineation Study Ons
Hipaa Challenge Exam Flashcards Quizlet

Mitigating Domestic Terrorism And Insider Threat Risks Security Magazine

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

The Three Elements Of Incident Response Plan Team And Tools

Scientific Program Of 34th World Congress Of Endourology Swl Program Book And Abstracts Journal Of Endourology

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

Hipaa And Privacy Act Training Pre Test Answers Pdf 1 In Which Of The Following Circumstances Must An Individual Be Given The Opportunity To Agree Course Hero

Pdf Development And Utility Of An Online Module Based On Nigerian Code Of Health Research Ethics Clement Adebamowo And Olubunmi Ogunrin Academia Edu

Healthcare Law Update July August 2022 Brach Eichler
A Huge List Of Cryptocurrency Thefts By Rokkex Hackernoon Com Medium

D Arcy Duquette Dvcjduquette Twitter

Which Of The Following Are Breach Prevention Best Practices Public Health